Splunk自定义威胁情报命令
事前准备
配置 VSCode 调试插件
分别在 Splunk 和 VSCode 上安装对应的插件:Splunk Add-on for Microsoft Visual Studio Code 和 Splunk Extension
在VSCode的settings.json中配置Splunk:
1 | "splunk.spec.FilePath": <$SPLUNK_HOME/etc/system/README/>, |
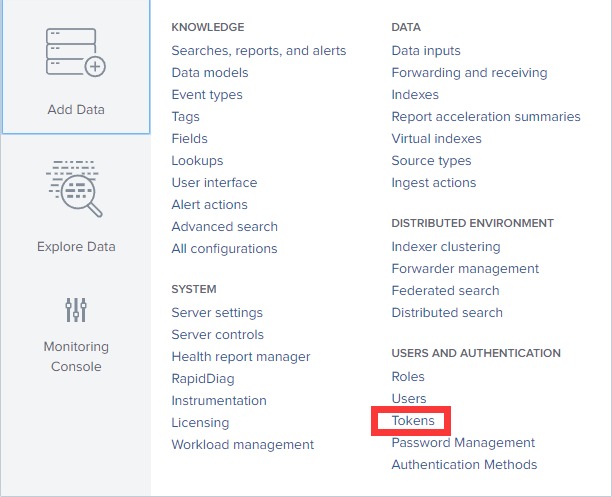
token 获取方法(Splunk系统必须启用KVStore):
配置 Splunk 调试插件
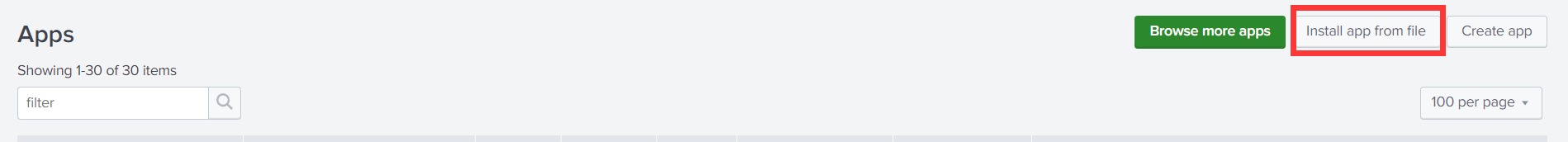
在 Splunk Web 界面上打开 Manage Apps 界面,直接点击 Install app from file 按钮,将 Splunkbase 上下载的安装包直接导入即可。
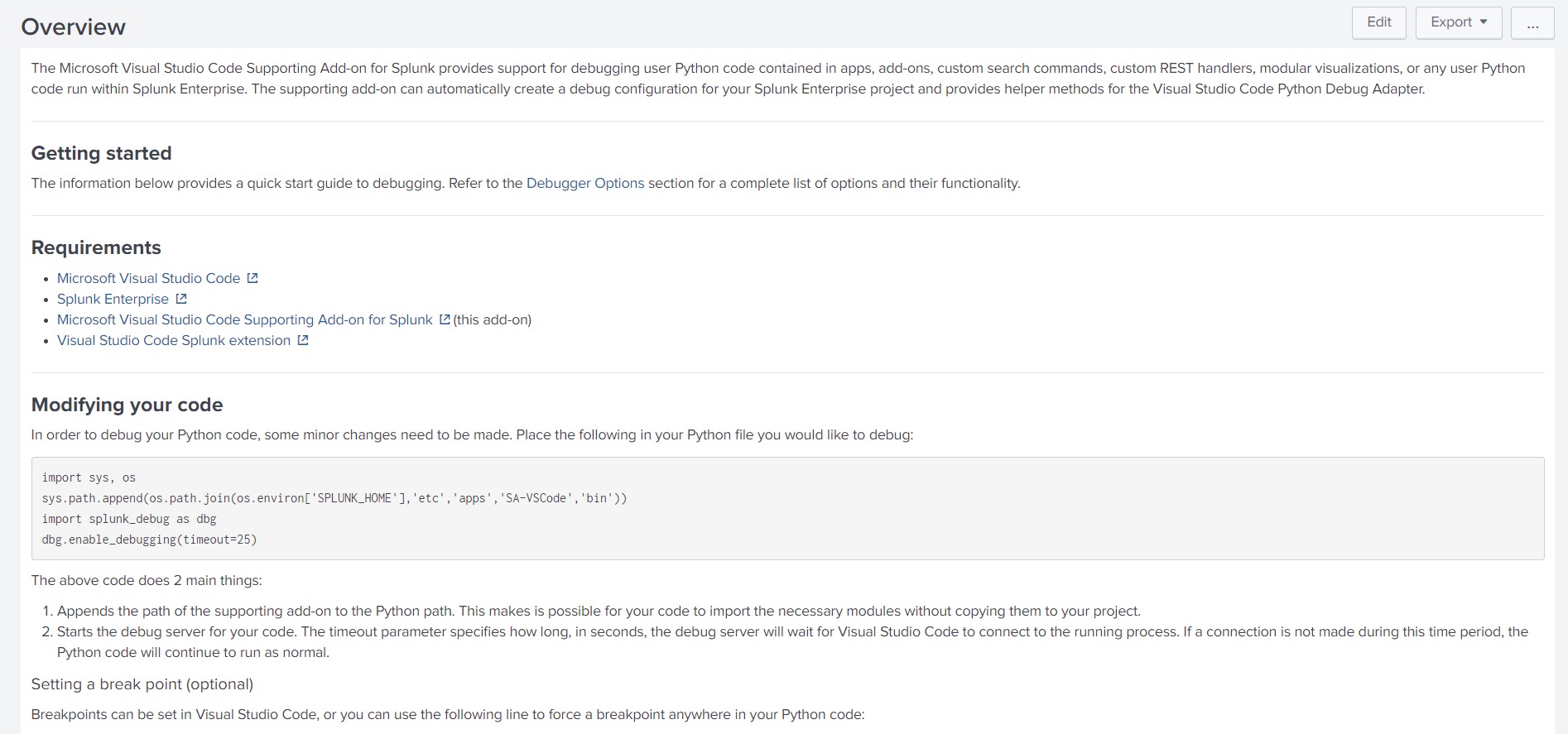
安装完成之后,可以看到 Apps 中已经存在 Microsoft Visual Studio Code Supporting Add-on for Splunk 这个App,打开 App 可以看到调试方法。
使用自定义脚本模板开发
打开 VSCode 命令面板(Ctrl+Shift+P),输入 Splunk ,找到VSC插件内置好的脚手架:
下载Splunk-SDK
使用下方命令将 splunk-sdk 安装到自定义Apps的 \bin 目录下①:
1 | pip install -t $SPLUNK_HOME/etc/apps/<APP_NAME>/bin splunk-sdk |
同理,安装其他第三方库也可以用同样的命令:
1 | pip install -t $SPLUNK_HOME/etc/apps/<APP_NAME>/bin <install-pip-package> |
编写脚本
Github传送门: xThreatBook
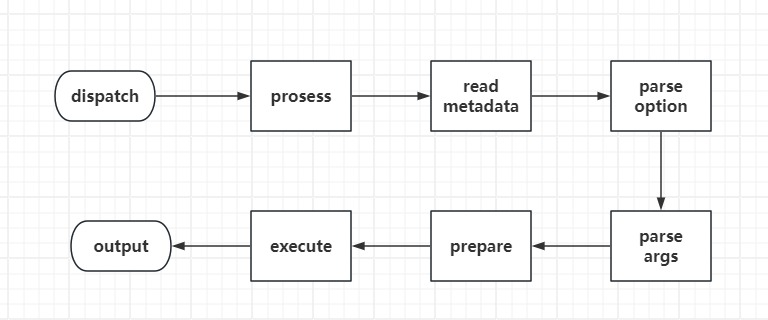
执行流程
添加提示信息
根据官方文档,编写如下提示信息:
1 | [threatinfo-command] |
注释
pip install 参数解释
使用 pip help install 命令可以看到对应解释:
1 | -t, --target <dir> Install packages into <dir>. By default this |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Peony!